Good practices : Websites security
Desenmascara.me goal: to raise security awareness among web owners in order to help decrease the constant rise of compromised websites.
For a full reference of this service check it out here.
Overview
Lot of people asked me how to improve the scoring of their websites. This mini-guide is aimed primarily at technical web owners. Knowing some useful security headers and some basics about web infrastructure can help you increase the security of your website. Just bear in mind that the below headers are browser dependent,
for more details check it out their support in the different browsers.
Desenmascara.me uses information as below besides another metadata to score web security awareness, the most signs of presence of this hardening configurations the most security aware a web site owner would be.
And remember; one of the key aspects is to keep update your website with the last and patched versions of the software used.
Index
Security HTTP headers
During the last years several HTTP headers have been introduced to help enhancing the security of a website. Usually these headers can be set in web server configuration without changing actual application's code. This offers significantly faster and cheaper method for at least partial mitigation of existing issues, and an additional layer of defense for new applications.
List of useful HTTP headers. Each of these HTTP headers detected by desenmascara.me will score with 20 points each one.
Let's see in more details which security
HTTP headers exists out there and their purpose:
Content Security Policy (CSP)
HTTP header:
Content-Security-Policy
Helps detect/mitigate XSS, mixed-content, and other classes of attacks. In Europe, despite having a directive which states:
"third party services are not allowed on Europa", no one is following it.
[1],
[2]. Therefore this header comes handy to allow you to create a whitelist of sources of trusted content, and instruct the browser to only execute or render resources from those sources. Read more in:
"an introduction to Content Security Policy".
Refs:
Wikipedia &
CSP on Chrome APPs.
Pwnedwebsites due to the lack of this protection: Reuters
HTTP Strict Transport Security (HSTS)
HTTP header:
Strict-Transport-Security
Ensures the browser never visits the http version of a website. Protects from SSLStrip/Firesheep attacks.
Threats addressed.
Refs:
RFC 6797 &
OWASP.
Pwnedwebsites due to the lack of this protection: N/A (here the pown goes to the client side)
X-Frame-Options (XFO)
HTTP header:
X-Frame-Options
Prevents your content from being framed and potentially clickjacked.
Refs:
Mozilla,
Django &
OWASP.
Pwnedwebsites due to the lack of this protection: Twitter
X-XSS-Protection
HTTP header:
X-XSS-Protection
Cross site scripting heuristic filter for IE/Chrome
Refs:
IEBlog &
MSDN.
Pwnedwebsites due to the lack of this protection: N/A (here the pown goes to the client side)
X-Content-Type-Options
HTTP header:
X-Content-Type-Options: nosniff
Sending this response header will prevent Internet Explorer from MIME-sniffing a response away from the declared content-type
Refs:
IEBlog &
Firefox team discussion to implement it.
Pwnedwebsites due to the lack of this protection: N/A (here the pown goes to the client side)
X-Download-Options
HTTP header:
X-Download-Options: noopen
The user is prevented from opening a file download directly; instead, they must first save the file locally.
Refs:
MSDN &
IEBlog &
MSDN blog.
X-Permitted-Cross-Domain-Policies
HTTP header:
X-Permitted-Cross-Domain-Policies:
Restrict Adobe Flash Player's access to data
Refs:
Adobe &
Flash Security.
Pwnedwebsites due to the lack of this protection: Google Docs
Web Architecture
Web site architecture is the approach to the design and planning of websites that involves technical, aesthetic and functional criteria. Here I will focus mainly in the security area within the technical criteria.
There are plenty of approaches to secure a web architecture but let's see very briefly the most common one:
Reverse proxies
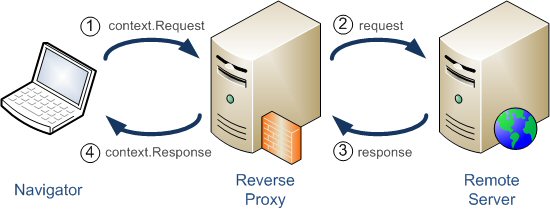
The most simple architecture of a reverse proxy
<pedantic mode on> Also know as
surrogates </pedantic mode off>.
There are serveral concepts related to a reverse proxy architecture such as:
load balancing, SSL termination, caching, URL rewriting and so on
but here the important thing is to understand the role of the most simple reverse proxy: an intermediary for its associated clients (web requests coming from Internet) to contact a web server. Therefore hiding the topology and characteristics of your websites/backends by removing the need for direct accesso to them.
Applying the concept of
defense in depth
Refs:
Wikipedia &
Web Caching by Duane Wessels (Old but one of the best books I have ever read about how proxies work. The core concepts are the foundations of how Internet work and still valid.).
Websites with reverse proxy architecture: Youporn
Application firewalls
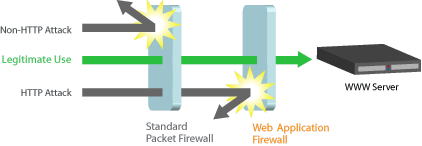
Application Firewall concept. L7 layer
Ryan Barnett who is the
ModSecurity project lead says the following about the term
Virtual Patching. Virtual Patching is a security policy enforcement layer that prevents the exploitation of a known vulnerability. The virtual patch works because the security enforcement layer analyzes transactions and intercepts attacks in transit, so malicious traffic never reaches the web application.
Applying the concept of
defense in depth in the same way as reverse proxies but with different goals.
Refs:
Web Application Firewall Criteria &
Owasp.
Websites with application firewalls architecture: Playboy
CDNs
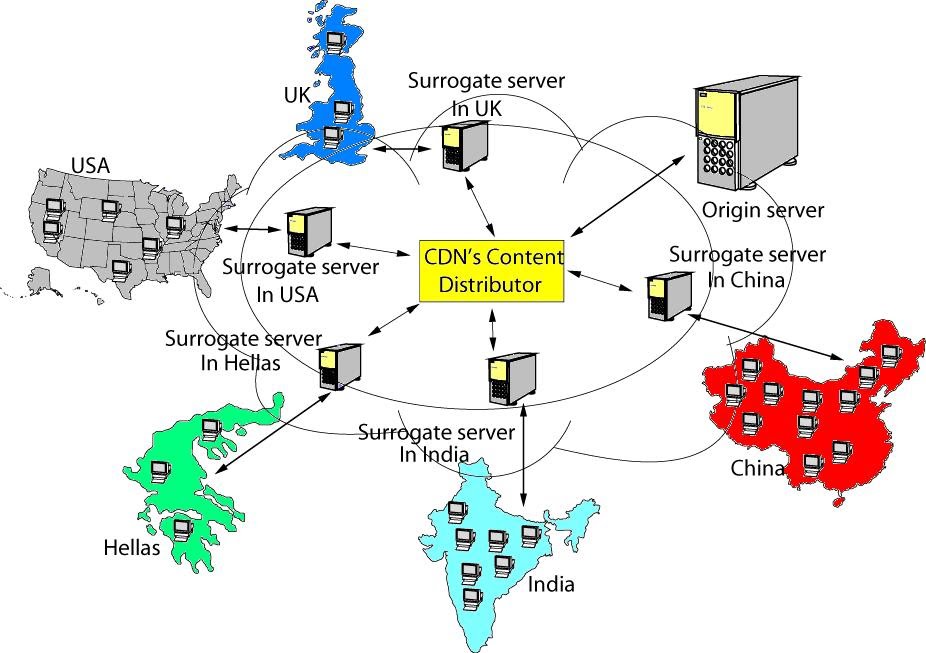
CDN graphic with servers distributed around the world
CDN (Content Delivery Network) is a large distributed system of servers deployed in multiple data centers across the Internet. The goal of a CDN is to server content to end-users with high availability and high performance. Its features and architecture make it ideal to act at the same time as reverse proxy and Application firewall.
Refs:
Wikipedia &
Akamai.
Websites with CDN architecture: CIA
Useful resources
If you want to add/fix/modify any aspect of this mini-guide please contact with me through the
contact form.
Many thanks.


